Deep dive into the operations of the EditBot stealer
I-TRACING CTI analysts performed a thorough investigation on the EditBot stealer’s operations. Discover how to protect yourself from this trivial social engineering attack that could nonetheless have significant impact.
Table of Contents
EditBot was first reported in mid-September 2023, by the cybersecurity providers Gardio and Cyble. The EditBot stealer is specialized in gathering passwords from browsers installed on the victim’s machine. At the end of the year 2023, our I-TRACING CTI Team got interested in tracking this activity cluster.
- EditBot may be related to another piece of malware reported earlier by Meta called NodeStealer. Their similarities have been highlighted by Netskope. Even if EditBot seems to be a complete rewrite of the NodeStealer, we confirmed they significantly overlap:
- Both info stealers are developed in a scripting language (NodeStealer in NodeJS, EditBot in Python).
- Both target the same browsers (the Vietnamese browser Cốc Cốc excluded in NodeStealer)
- Both embed their own scripting interpreter because of the use of scripting languages not deployed by default with Windows.
- The distribution methods of both info stealers are similar. As observed in May 2023 and September 2023 by Meta and Gardio, initial infection occurs with private messages sent through social media accounts such as Facebook. Written in English, the message usually uses a false reason based on product reviews or inquiries to send compressed archives.
This archive contains a batch script loader that will retrieve another archive from the Command and Control (C2) server, unzip and execute the final payload. The second-stage archive is a portable version of the Python interpreter along with a Python script specialized for Windows. This last script will read secrets from common browsers and exfiltrate them to a Telegram or Discord channel owned by the attacker.
Key Takeaways from the investigation
The investigation highlighted that:
- Malware operators likely originate from Vietnam (language used, hosting used, Vietnamese browser targeted)
- Threat actors combined several deployment methods for C2 servers: usage of open-source platforms like GitHub, public Cloud storage like MediaFire and domain name hijacking or purchase.
- Exfiltration occurs through messaging platform APIs such as Discord and Telegram.
- C2 servers change roughly every 2 weeks as well as the Telegram bot for data exfiltration.
- Infrastructure is hosted behind Cloudflare, but some instances allowed to observe the use of a Vietnamese bulletproof hosting service named “dichvudark”.
EditBot stealer origins and operations
A social media message at the source of it all
I-TRACING CTI Team got their hands on malicious messages sent by the threat actor on social media platforms. These messages, originating from an unknown contact, were brief, written in proper English, and did not anticipate a response as the payload was directly sent.
Interestingly, we observed a shift in the behavior. Prior to December 2023, the threat actors behind or using EditBot relied on various distribution methods, showing a preference for open-source platform repositories, according to Cyble. Moreover, the chain leading to compromise was considerably simpler, occasionally featuring the malware directly. Additionally, the use of command and control servers was not consistently employed.
However, starting in December 2023, we observed that several servers were hosted by dichvudark[.]vn, a seemingly Vietnamese bulletproof hosting provider. Since then, these servers have been rotated roughly once every couple of weeks and were provided by various hosting companies.
EditBot stealer installation and delivery
The first archive sent through social media instant messaging and customer portals contains a batch script retrieving the download PowerShell command from the dropper server. Once retrieved, the downloaded PowerShell command downloads the final payload in the form of an archive. This multi-stage deployment starts when the victim clicks on the file contained in the first archive.
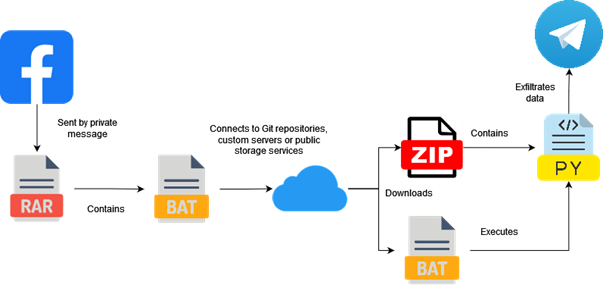
Figure 1: Delivery process of EditBot stealer
The BAT dropper downloads a second BAT file from a domain, Git repositories and public file hosting belonging to the attacker depending on the campaign and saves it in the user’s Programs\Startup folder. The script will be executed on each new session.
Along with the BAT file placed in the Startup folder, a ZIP file is downloaded. This archive will contain a portable Python interpreter and the actual info stealer payload. It is then executed using a command retrieved from the C2 server.
Finally, on execution, the info stealer will collect browser credentials and exfiltrate them through a Telegram bot.
Whenever a public cloud service is used, a username containing the mention “achung” is observed in nearly all occurrences. Gardio indicated back in September a similar name for a Telegram channel on which the info stealer was sending messages: “ACHUNG — 21/8 — ❤️❤️❤️”.
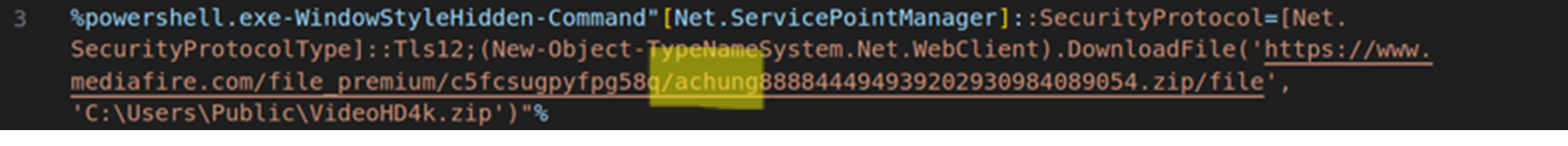
Figure 2: PowerShell command executed to download the EditBot info stealer’s malicious package containing “achung” in its name
The final payload is composed of a legitimate Python interpreter packaged with a lightly obfuscated Python script which is the actual info stealer:
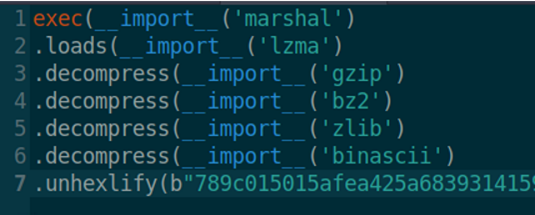
Figure 3: Obfuscation layers used in the EditBot stealer
The obfuscation process makes use of several layers of compression. At runtime, a hexadecimal representation of the compressed code is reversed to binary and passes through four different inflate functions. After inflation, the final Python code is passed to the exec function that will interpret it as code.
It is then possible to obtain the plaintext code by switching the exec function for the print function. As such execution in a Python interpreter will yield the cleartext source of the info stealer.
Deobfuscating EditBot’s Python script to better understanding this info stealer’s goals
When deobfuscated, reading the Python script reveals that this piece of malware uses the Windows API. As such, it is only able to properly work on Windows OS even though Python is natively multi-platform.
It also seems that the threat actors behind the EditBot stealer copied code from other sources as some comments associated with the password decryption routine are written in French when all other user text is in Vietnamese.
The info stealer aims nearly exclusively at exfiltrating passwords and cookies from browsers. It supports Google Chrome, Mozilla Firefox, Edge, Opera, Brave, other Chromium browsers and Cốc Cốc, a Vietnamese browser. It also collects the public IP address of the victim and system information.
The data is decrypted for each browser and then packaged into a zip file which will be sent to a Telegram bot. The identity of the bot changes with each two-weeks campaign.
Surprisingly, despite being lightly obfuscated, the malware detection rate stays low1. It has not changed much since the first report by Gardio in September 2023.
EditBot stealer C2 Infrastructure and tracking opportunities
Originally, EditBot used public source code platforms like GitHub to deliver its payload. It shifted during December 2023 to a dedicated infrastructure and/or compromised applications, preferably located behind Cloudflare. EditBot rotates its infrastructure roughly every couple of weeks.
Here is a list of the observed C2 infrastructure in the time frame of the investigation:
| C2 address |
|---|
| shoppingvideo247[.]com |
| school-us[.]store |
| ref-media[.]net |
| vuagame[.]store |
| clonecloneclonewhomanmale[.]site |
| breakingmyanmarnews[.]com |
At first, the threat actor seemed to register domains for each campaign. However, the last domain observed breakingmyanmarnews[.]com rather seems to be a defunct legitimate website taken over by the threat actor. This may indicate a shift in tactics in January 2024. Regular small changes in these tactics as this one seem to indicate that the threat actors are constantly adapting their operation to the opportunities of the moment.
While pivoting on domain names, I-TRACING’s CTI Team detected in the domain WHOIS information a possible affiliation to a group named “dichvudark”, a Vietnamese “Dark Services” platform.
Investigation confirmed by pivoting on IPs addresses that “dichvudark” provides BulletProof hosting services to EditBot infrastructure.
Figure 5: dichvudark[.]vn
I-TRACING’s CTI team was able to retrieve information such as the names of the bots, the name of the chats where the credentials are sent, as well as the names of administrators behind the chats. Even if the accounts differ from the ones reported by Gardio, there are overlaps in the naming conventions.
One of the chats was no longer active at the time of writing this report. I-TRACING’s CTI Team found that bots used in different versions of EditBot send their data in chats administered by the same person: ThaiTu7 / Black King.
| Username | Chat where credentials are sent | Administrator behind the chat |
|---|---|---|
| Idol_Pro_Bot | A Trung Pro 9999 ❤️❤️❤️ | ThaiTu7 / Black King |
| ref_data_bot | SOME EM Gái CǪ0NH NH<0 | Bitch_jo / MreR Jhone |
| Howbro2024_bot | N/A | N/A |
| AChung_VuaTienTe_Bot | ATrung 9999 ❤️◌️❤️◌️❤️ | ThaiTu7 / Black King |
Figure 12 : ThaiTu7 / Black King telegram profile of the administrator behind chats used by the EditBot stealer
EditBot stealer: spreading through trivial social engineering attack and easily remaining undetected
In conclusion, our I-TRACING CTI Team analysis corroborates the first elements given in September 2023 about a NodeStealer malware variant dubbed EditBot and targeting social media business accounts via social engineering attacks. A study of the code and infrastructure suggests that the attackers belong to a cluster based in Vietnam.
In addition, in late 2023, our I-TRACING CTI Team observed changes in the behavior and methodology of EditBot operators through several investigations. Changes occurred in the spreading mechanism and operator infrastructure. Thus, it appears that malicious code is no longer downloaded from open code repository platforms, but from public cloud storage, from dedicated domains or from compromised websites. Presumably to avoid detection, attackers keep changing their C2 server.
Even though a trivial phishing technique and a light obfuscation of a malware whose source code has not changed much since September 2023, the antivirus detection rate remains low. Finally, in opposition with the absence of significant changes in the malware source code, the changes in the threat actors’ methodology are hints of a non-industrial process that keeps adapting depending on technical constraints.
Appendix
Indicators of compromise (IoCs)
| Type | Value | Description |
|---|---|---|
| Domain | breakingmyanmarnews[.]com | EditBot download site |
| Domain | clonecloneclonewhomanmale[.]site | EditBot download site |
| Domain | ref-media[.]net | EditBot download site |
| Domain | school-us[.]store | EditBot download site |
| Domain | vuagame[.]store | EditBot download site |
| Domain | shoppingvideo247[.]com | EditBot download site |
| URL | hxxps[://]www[.]mediafire[.]com/file_premium/c5fcsugpyfpg58q/achung888844494939202930984089054[.]zip/file | EditBot download URL |
| SHA-256 | 098672353240df8cbbb7487ad1e3df3e25ceae3ad1dc84e451f03b803183e86a | |
| SHA-256 | 10372d23b54e550926e59ec359aadf5180e9839cf20086473422d55b444353d6 | |
| SHA-256 | 12444acca1f75247e756516a5d3ca2a33d67641f0664c00c3220f141b3dd8ce1 | RAR archive |
| SHA-256 | 171169cf8c15ae6404f3849274fdbbe0cabc4f3ec0b65a3441228b1dbe31a0d6 | |
| SHA-256 | 1af8a147d6e77ffcbf8e5dda14b32c715c4149b5e1c933fa69e451600ecfbf8e | RAR archive |
| SHA-256 | 1c8482f6df65440bf98fdceddac178e841bc801f591de6b060c45b50136dff1f | |
| SHA-256 | 201d67748c9647ca7a6f504a93535f391c5c5fb51a756c840d21f55d06300fcc | Stealer ZIP file |
| SHA-256 | 2ed49926c05f11f9259848d24db0292f8af3e3656d4213edcbc0e4e9d3547998 | Dropper BAT file |
| SHA-256 | 377d76add32b18c33c0ade90cb355a1e9f0ead3b9a7060f56557fb1fe1b39434 | |
| SHA-256 | 3b0424a252a5cbadbb870907ed3c118cafc01ae86382f1775de5b9bc6cc3bce3 | |
| SHA-256 | 3b99507af4fd76810ec8224122bc3701f7f2ef2cfa9677d012854df3abd44f5c | |
| SHA-256 | 3bf11184b67b82e367d36cb9ed3380a43814b000d84aef0bb89d4e08e4fcd581 | RAR archive |
| SHA-256 | 3f302fb736164983f04a9ebb8e2ab5604bb92380e8ccac8b160698fb02ccaebd | |
| SHA-256 | 3f7bd47fbbf1fb0a63ba955c8f9139d6500b6737e5baf5fdb783f0cedae94d6d | Stealer Python script |
| SHA-256 | 40f06539ed0d45ba833d6ff0b9ef8165b8bebf407abcf17f27ec27951de0d513 | BAT File for persistence |
| SHA-256 | 463a5ad91dd8adc56d700c059770de8ee01b3ba5bc276d17db872cc69d6768bf | |
| SHA-256 | 474d1dcec292401ade40bd90a95b872e5ab2c8fb68737b786e4308444d3ad33a | RAR archive |
| SHA-256 | 4883379040196cb4362ed4dfe4c011512febbfac7217e029f107b62c9acce6df | |
| SHA-256 | 4b977d4e522186d89559821c675a14d31f367c67e3418a2cc74d72c405832efa | Dropper BAT File |
| SHA-256 | 548acae9620f6541fa647dcbfe7ed2f3d9637f228b24bfcb0c7d17f34e83b8e5 | |
| SHA-256 | 54cf73082944d966e232d74c33f0cd4e05411846d57fab35171369910be84eb1 | |
| SHA-256 | 57ecb84193e327b58a62663d5e34d96503bbd81c461f91780b4f6bdb9fc4aabf | |
| SHA-256 | 82c29d1bbb6ef9f3aff4d3ca91f3ec6dfc17018ec0e6da32d080658a19502db6 | |
| SHA-256 | 91dff3d1e940290529d064a0b13e190e6231679ea067df399de559d5bd071d81 | RAR archive |
| SHA-256 | 97252bdb029fcdc9cfda86688a6327f76ea780761a3c1736db6a368ea30ffa14 | |
| SHA-256 | 9d048e99bed4ced4f37d91a29763257a1592adb2bc8e17a66fa07a922a0537d0 | Dropper BAT File |
| SHA-256 | 9dd9cc235f8c2c753529955a351805e01229cc5052932561b0b96344537ce46c | |
| SHA-256 | 9f1711a6157ba51b8e464ff4659c3a1db036e2e93721263e0091ed6fe53bf503 | |
| SHA-256 | a39f0c56dd602fcc14adcdeaa31c21d389af8ea8abcb89862fac19e2807c799d | RAR archive |
| SHA-256 | aa3fde3269b630ce09e882ed0224b2271ebda197f5e5e4beb69994e9fc8ddc44 | |
| SHA-256 | aaa953d2e18d4620a4a6e60c42f67a6e07cab05eec50e6e8f16f19cfa7c1d13b | |
| SHA-256 | b14a6391e11fe1e2bbf9972e5fefb7579bfcb4177acf60bcf1fc39fdacd1ddfa | |
| SHA-256 | b31c3c0887543b08df40a0a55718bc3686a6025f24a8b6e9a5d275a90c637c37 | ZIP file |
| SHA-256 | bc3993769a5f82e454acef92dc2362c43bf7d6b6b203db7db8803faa996229aa | Dropper BAT File |
| SHA-256 | bca1c784742fc086d381f4e1e4495941626d1b829147d0d5f6d3f47af78364dd | RAR File |
| SHA-256 | c116663954c00ef7be0ce7d391bed95fe0c1f775b97652906c49ec3fcd814719 | RAR File |
| SHA-256 | c8af31d897d7e2ee9babb6a60dec5b65fc4b018e4ce8da6a5d8008ce5926bd54 | |
| SHA-256 | c93a22032bf5cf29ed22065ce572caca41152281852f8b81e034e1e64f4057f4 | |
| SHA-256 | d0237b6e1ab07c8300ad282ed3aa1f6e0e90220d893bbeee26786e886cedb9ad | RAR File |
| SHA-256 | d13aba752f86757de6628e833f4fdf4c625f480056e93b919172e9c309448b80 | Dropper BAT File |
| SHA-256 | e3579f1112a695c5117dff5830ef64bf47703943e7ee7dbd32086c7865fcf126 | |
| SHA-256 | e7cd3233fd39175970675135dac2c582382747b328b3786f8a833ae2ab8f4239 | RAR File |
| SHA-256 | f1ff46c4dd8ebbf092a38910796a1e1adb455bf476a2405ad315c5e37afc3e99 | Stealer Python script |
| SHA-256 | fd8391a1a0115880e8c3ee2e76fbce741f1b3c5fbcb728b9fac37c21e9f6d7b7 | RAR File |
TTPs
| Tactic | Technic ID |
|---|---|
| Initial Access (TA0001) | Phishing (T1566) |
| Execution (TA0002) | Command and Scripting Interpreter (T1059.001) |
| Discovery (TA0007) | Process Discovery (T1057) |
| Persistence (TA0003) | Startup Folder (T1547.001) |
| Collection (TA0009) | Data from the Local System (T1005) |
| Credential Access (TA0006) | Steal Web Session Cookie (T1539) |
| Credential Access (TA0006) | Credentials from Password Stores (T1555) |
| Exfiltration(TA0010) | Exfiltration Over Web Service: Exfiltration Over Webhook (T1567/004) |
Sources
- Cyble. (n.d.). New Editbot Stealer Spreads Via Social Media Messages. Retrieved from https://cyble.com/blog/new-editbot-stealer-spreads-via-social-media-messages/
- Gardio. (n.d.). “MrTonyScam” — Botnet of Facebook Users Launch High-Intent Messenger Phishing Attack on Business Accounts. Retrieved from https://labs.guard.io/mrtonyscam-botnet-of-facebook-users-launch-high-intent-messenger-phishing-attack-on-business-3182cfb12f4d
- Meta. (s.d.). The malware threat landscape: NodeStealer, DuckTail, and more. Récupéré sur https://engineering.fb.com/2023/05/03/security/malware-nodestealer-ducktail/
- Netskope. (n.d.). New Python NodeStealer Goes Beyond Facebook Credentials, Now Stealing All Browser Cookies and Login Credentials. Retrieved from https://www.netskope.com/blog/new-python-nodestealer-goes-beyond-facebook-credentials-now-stealing-all-browser-cookies-and-login-credentials
Author
Louis Pariente, CTI analyst | I-TRACING
01 August 2024


